Before we start, a story. When I created my first web server, I’d found a copy of Windows NT Server 4.0, upgraded it to Service Pack 6a to get IIS enabled, opened port 80 on the router and viola, working webserver. This was 2001 and unfortunately my creation of a webserver coincided with the spread of the Code Red virus, and it reached my server within days of it being online.
Not knowing at the time, and thinking it was a one off, formatted the hard drive and completed the whole setup again. A day passed before the virus was back. Now with the knowledge of what was happening and wary of it happening again. I rebuilt the server and this time put the website behind port 8080, this time the virus never returned.
I thought to myself that this was security through obscurity, and with the victory over Code Red, was something I held onto for many years.
I applied this method when it came to opening RDP access to the outside world, choosing a seemingly obscure port 8021 on each network setup. However, I’ve been dealt a wakeup call following what I’ve just seen…
In my small flat I have the advantage / disadvantage dependant on opinion of having my network switch located below my TV in the living room, allowing me to glance at network activity quite easily. Paying attention, the port to the server and router uplink had been constantly transferring data, this is not unusual as the is a webserver on it and with all WordPress based websites has many an attack attempts each day.
What was different the last few days is that the transfer was constant, instead of an organic flashing pattern, where you can almost visualise each web request and response, it was a steady stream, and lasted well beyond the reason of any process I could think of.
Curiosity overwhelming me, I remoted on to the server and looked at the network tab of the resource monitor, only to be greeted by this:
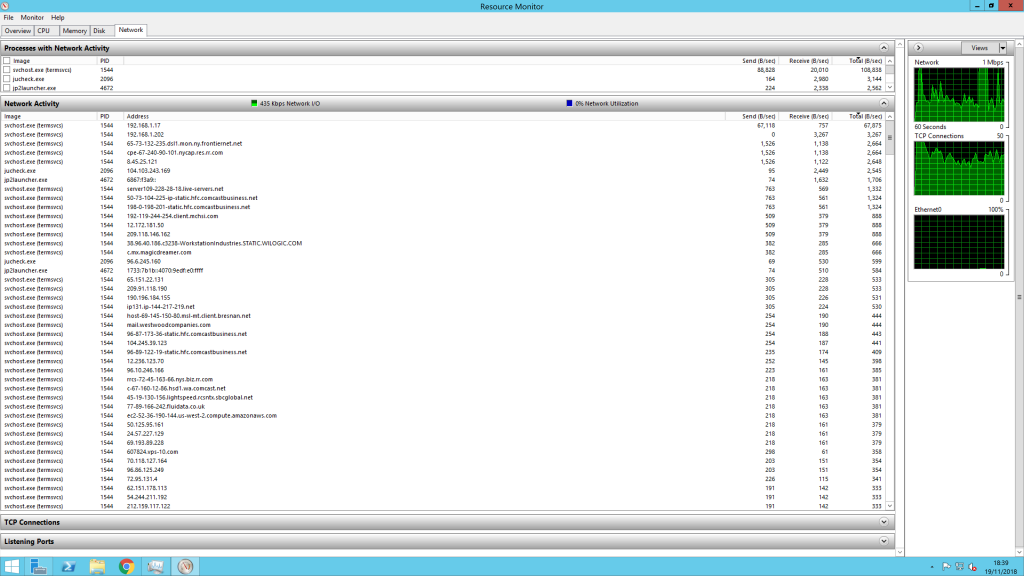
Around 50 unknown address all connecting to terminal services. After the initial shock I read more into and based on the network throughput of each IP compared to my active RDP connection (Here is 192.168.1.17) believe they were still at the brute force stage of logging in.
Looking further this looked to be more of a botnet of compromised machines, as hostnames comprise of generic consumer connections, Amazon EC2 and even a mail server.
The forwarding port on the router was quickly closed and the connections soon reduced
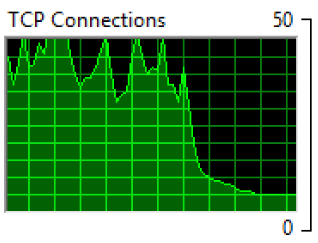
This is my self-lesson, security by obscurity is no longer an option. With exponentially more bandwidth and processing power available to the world, not to mention the amount of devices online compared to my beginnings in 2001, you can hide, but they will find you.